Electronic Warfare A Primer
The nature of electromagnetic propagation ensures that when a wireless signal such as a Wi-Fi network, Personal Mobile Radio (PMR) or car remote key fob is used, it is not solely directed to the intended recipient, instead it is broadcast openly and is limited only by the rules of physics and the interplay of the physical waveform and its surrounding environment.
Given these constructs, equipment such as Low Noise Amplifiers, Directional Antennas and signal processing techniques can allow an adversary to recover signals far beyond their intended range. This ensures that no wireless transmission can ever be regarded as private and confidential. Given the increasing amount of personal data relating to banking, safety of life being transmitted via wireless networks, the requirement to protect against an adversary increases.
Protection mechanisms exist to increase the protection of a systems Confidentiality, Integrity or Availability, however the cycle of protection mechanism and eventual defeat via threat technology is testament to the continued vulnerability of these systems.
The wireless threat environment was restricted to those that possessed specialist knowledge and expensive equipment. These were normally Radio Ham operators who had access to limited equipment or Governmental/Military specialists who had access to both complex equipment and the training to conduct these attacks. Developments of Bits to RF direct conversion, enabling a new generation of cheap Software Defined Radios have removed these limitations in terms of access to technology, and the Internet has democratised the access to knowledge leaving a potent mixture of enhanced risks that wireless networks are now exposed to. Given the ubiquitous nature and the sensitivity and safety in relation to data that is now passed over these connections, threats that were once related only to a military operation are now potential attack vectors that should be taken into account within civilian infrastructure and military systems alike.
Systems can come under attack via three different vectors. These seek to counter the three modes of protection; Confidentiality, Integrity and Availability. Interception seeks to extract the information being communicated by a system, whether it’s the digital payload or an analogue encoded voice message.
Interception
Normally requires the third party to extract the information without affecting the integrity of the signal in question, however within a wireless system this is not required as passive techniques can be used to de-modulate and de-code the signal of interest without the target being aware. Due to this, it is difficult to detect an intercept attack that is in progress on a wireless network. These attacks can be carried out against the prime Radio Frequency (RF) emanations or against the unintentional RF emanations from electronics (a practice that has been given the code name of TEMPEST by western governments).
Figure 1: Wireless Intercept
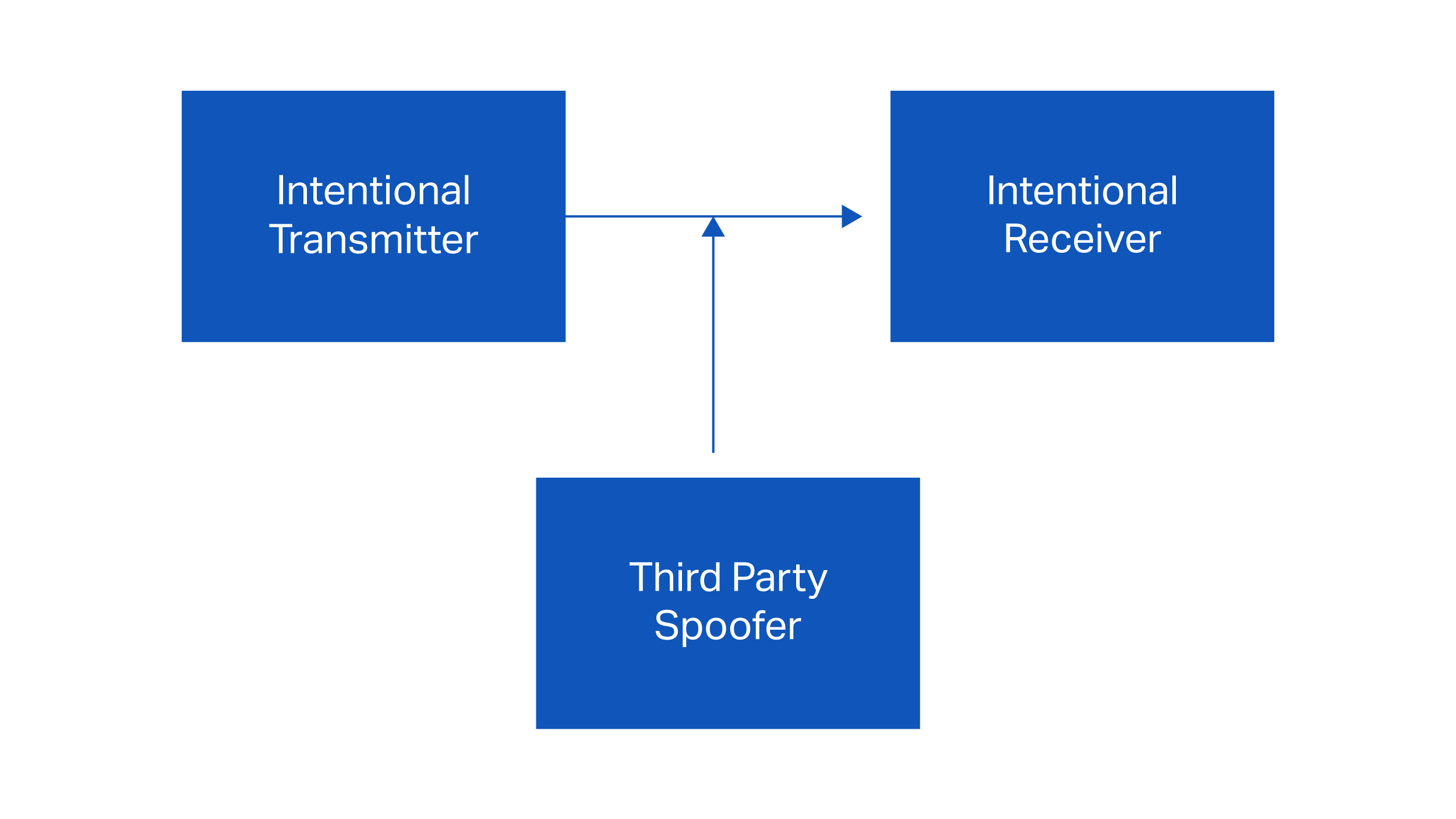
Spoofing
Typically involves injecting crafted packets into wireless systems causing either subtle effects, for instance an increase in Bit Error Rate (BER), or bulk errors in data. One of the most prominent examples of spoofing is the corruption of Global Positioning System (GPS) location data. Recent sources (Christian Science Monitor , 2011) have indicated that downing of a USA Department of Defence (DoD) Unmanned Air Vehicle was related to GPS spoofing activity, however this has not been officially confirmed by the US air force. The detection of spoofing events is feasible due to the active nature of the signal injection; however, a well-crafted spoof attack leaves no residual signature after the attack.
Figure 2: Spoofing
Jamming
he process of injecting noise into a RF channel in order to deny its availability. There are various jamming techniques varying from Barrage, which indiscriminately blocks single or multiple radio channels; Reactive, which seeks to stay silent until the target waveform is detected; or protocol, where the protocol layer of the wireless signal is interfered with to disrupt its operation. Jamming attacks, by their nature, are noisy and easy to detect, however when conducted with sufficient power they are difficult to counter, unless the target systems have sufficient RF bandwidth that spreads the signal past the capabilities of the jammer. Jamming although easily identifiable is the easiest attack vector against wireless networks not requiring fundamental knowledge of the target waveform. Distributed and co-ordinated jammers have the potential for blocking access to wireless services Electronic Warfare A Primer Issue 1 over a large area. If applied to a service such as Tetra in the UK, could remove access to primary Blue Light emergency communications for a local area.
Figure 3: Jamming
When Electronic systems are designed, Security of electronic systems, whether wireless or wired can be protected from three different factors; the Confidentiality, Integrity or Availability of the information that is being either processed, communicated or stored.
Within the Defence and Security environment. It is easy to understand that within this environment there is a direct correlation between the vulnerability of a wireless system and its impact on the safety of persons.
Wireless systems are used to pass information relating to the command and control of specific military capability. This could be a formation of troops, vehicles or large platforms such as a Submarine, Ship or Aircraft. These communication systems have been well protected in order to ensure their continued operation when under attack from a third party, preventing disruption to their operation. In this scenario it is perceivable that a vulnerability within the wireless connection could lead to a fire control order being erroneously raised, prior knowledge of an attack being gained or even direct control of a remote weapon system.
Various open media organisations have previously reported on real world examples where the Predator drone video downlink had been intercepted and used by insurgent actors in order to gain an understanding of the Predator operations against them. This relied on intercepting and decoding the signal that was being used by forward deployed soldiers to watch insurgent activity, clearly highlighting the existing threat in symmetric as well as asymetric threat environments.
As military communication adopts a more commercial based architecture, the security of these waveforms and modulation techniques require deeper analysis. In contrast the commercial use of these waveforms and protocols need protection from Intercept as the EW threat that used to be confined to nation state actors, such as Intelligence or Military units, is now available to hobbyists and hackers alike, providing an increased likelihood of the threat.
Interested in this subject?
Get in touch, we are happy to provide assistance and training